

Cybersecurity Business Plan Template
Written by Dave Lavinsky

Over the past 20+ years, we have helped over 500 entrepreneurs and business owners create business plans to start and grow their cybersecurity companies.
If you’re unfamiliar with creating a cybersecurity business plan, you may think creating one will be a time-consuming and frustrating process. For most entrepreneurs it is, but for you, it won’t be since we’re here to help. We have the experience, resources, and knowledge to help you create a great business plan.
In this article, you will learn some background information on why business planning is important. Then, you will learn how to write a cybersecurity business plan step-by-step so you can create your plan today.
Download our Ultimate Business Plan Template here >
What is a Cybersecurity Business Plan?
A business plan provides a snapshot of your cybersecurity business as it stands today, and lays out your growth plan for the next five years. It explains your business goals and your strategies for reaching them. It also includes market research to support your plans.
Why You Need a Business Plan for a Cybersecurity Company
If you’re looking to start a cybersecurity business or grow your existing cybersecurity company, you need a business plan. A business plan will help you raise funding, if needed, and plan out the growth of your cybersecurity business to improve your chances of success. Your cybersecurity business plan is a living document that should be updated annually as your company grows and changes.
Sources of Funding for cybersecurity Businesses
With regard to funding, the main sources of funding for a cybersecurity business are personal savings, credit cards, bank loans, and angel investors. When it comes to bank loans, banks will want to review your business plan and gain confidence that you will be able to repay your loan and interest. To acquire this confidence, the loan officer will not only want to ensure that your financials are reasonable, but they will also want to see a professional plan. Such a plan will give them the confidence that you can successfully and professionally operate a business. Personal savings and bank loans are the most common funding paths for cybersecurity companies.
Finish Your Business Plan Today!
How to Write a Business Plan for a Cybersecurity Business
If you want to start a cybersecurity business or expand your current one, you need a business plan. The guide below details the necessary information for how to write each essential component of your cybersecurity business plan.
Executive Summary
Your executive summary provides an introduction to your business plan, but it is normally the last section you write because it provides a summary of each key section of your plan.
The goal of your executive summary is to quickly engage the reader. Explain to them the kind of cybersecurity business you are running and the status. For example, are you a startup, do you have a cybersecurity business that you would like to grow, or are you operating a chain of cybersecurity businesses?
Next, provide an overview of each of the subsequent sections of your plan.
- Give a brief overview of the cybersecurity industry.
- Discuss the type of cybersecurity business you are operating.
- Detail your direct competitors. Give an overview of your target customers.
- Provide a snapshot of your marketing strategy. Identify the key members of your team.
- Offer an overview of your financial plan.
Company Overview
In your company overview, you will detail the type of cybersecurity business you are operating.
For example, you might specialize in one of the following types of cybersecurity businesses:
- Remote security center services : This type of cybersecurity is focused on providing comprehensive security for networks and devices remotely from a main control center.
- Cloud security services . As more businesses turn to storage in cloud platforms, this type of service protects the data of clients from being utilized by others in that platform.
- Vulnerability scan & management: This service screens client devices and network systems remotely on a monthly maintenance basis.
- Endpoint security services: This service is dedicated to the mobile and end user devices in corporate offices; protection for computers is not included.
In addition to explaining the type of cybersecurity business you will operate, the company overview needs to provide background on the business.
Include answers to questions such as:
- When and why did you start the business?
- What milestones have you achieved to date? Milestones could include the number of security breaches determined, the amount of revenue earned, or reaching X number of clients served, etc.
- Your legal business Are you incorporated as an S-Corp? An LLC? A sole proprietorship? Explain your legal structure here.
Industry Analysis
In your industry or market analysis, you need to provide an overview of the cybersecurity industry.
While this may seem unnecessary, it serves multiple purposes.
First, researching the cybersecurity industry educates you. It helps you understand the market in which you are operating.
Secondly, market research can improve your marketing strategy, particularly if your analysis identifies market trends.
The third reason is to prove to readers that you are an expert in your industry. By conducting the research and presenting it in your plan, you achieve just that.
The following questions should be answered in the industry analysis section of your cybersecurity business plan:
- How big is the cybersecurity industry (in dollars)?
- Is the market declining or increasing?
- Who are the key competitors in the market?
- Who are the key suppliers in the market?
- What trends are affecting the industry?
- What is the industry’s growth forecast over the next 5 – 10 years?
- What is the relevant market size? That is, how big is the potential target market for your cybersecurity business? You can extrapolate such a figure by assessing the size of the market in the entire country and then applying that figure to your local population.
Customer Analysis
The customer analysis section of your cybersecurity business plan must detail the customers you serve and/or expect to serve.
The following are examples of customer segments: government contractors, for-profit corporations, securities businesses, private security services, and individuals.
As you can imagine, the customer segment(s) you choose will have a great impact on the type of cybersecurity business you operate. Clearly, government contractors would respond to different marketing promotions than individuals, for example.
Try to break out your target customers in terms of their demographic and psychographic profiles. With regards to demographics, including a discussion of the ages, genders, locations, and income levels of the potential customers you seek to serve.
Psychographic profiles explain the wants and needs of your target customers. The more you can recognize and define these needs, the better you will do in attracting and retaining your customers.
Finish Your Cybersecurity Business Plan in 1 Day!
Don’t you wish there was a faster, easier way to finish your business plan?
With Growthink’s Ultimate Business Plan Template you can finish your plan in just 8 hours or less!
Competitive Analysis
Your competitive analysis should identify the indirect and direct competitors your business faces and then focus on the latter.
Direct competitors are other cybersecurity businesses.
Indirect competitors are other options that customers have to purchase from that aren’t directly competing with your product or service. Software companies, home or office hardware, and remote alarm services may be examples of indirect competitors. You will want to mention any direct competition, as well.
For each direct competitor, provide an overview of their business and document their strengths and weaknesses. Unless you once worked at your competitors’ businesses, it will be impossible to know everything about them. But you should be able to find out key things about them such as
- What types of customers do they serve?
- What type of cybersecurity business are they?
- What is their pricing (premium, low, etc.)?
- What are they good at?
- What are their weaknesses?
With regard to the last two questions, think about your answers from the customers’ perspective. And, don’t be afraid to ask your competitors’ customers what they like most and least about them.
The final part of your competitive analysis section is to document your areas of competitive advantage. For example:
- Will you provide discounts for major government contractors?
- Will you offer scan protection and management that your competition doesn’t?
- Will you provide better customer service?
- Will you offer better pricing?
Think about ways you will outperform your competition and document them in this section of your plan.
Finish Your Business Plan Today!
Marketing Plan
Traditionally, a marketing plan includes the four P’s: Product, Price, Place, and Promotion. For a cybersecurity business plan, your marketing strategy should include the following:
Product : In the product section, you should reiterate the type of cybersecurity company that you documented in your company overview. Then, detail the specific products or services you will be offering. For example, will you provide in-person and remote cybersecurity services for major corporations or will you offer compliance solutions for select clients?
Price : Document the prices you will offer and how they compare to your competitors. Essentially in the product and price sub-sections of your plan, you are presenting the products and/or services you offer and their prices.
Place : Place refers to the site of your cybersecurity company. Document where your company is situated and mention how the site will impact your success. For example, is your cybersecurity business located in a professional business district, a quiet corporate area, a standalone building or a remote, unnamed location? Discuss how your site might be the ideal location for your customers.
Promotions : The final part of your cybersecurity marketing plan is where you will document how you will drive potential customers to your location(s). The following are some promotional methods you might consider:
- Advertise in trade magazines
- Reach out to websites
- Engage in email marketing
- Advertise on social media platforms
- Improve the SEO (search engine optimization) on your website for targeted keywords
Operations Plan
While the earlier sections of your business plan explained your goals, your operations plan describes how you will meet them. Your operations plan should have two distinct sections as follows.
Everyday short-term processes include all of the tasks involved in running your cybersecurity business, including answering calls, planning and providing scan management, responding to emergency situations, billing clients and assisting with computer equipment, etc.
Long-term goals are the milestones you hope to achieve. These could include the dates when you expect to book your Xth client, or when you hope to reach $X in revenue. It could also be when you expect to expand your cybersecurity business to a new city.
Management Team
To demonstrate your cybersecurity business’ potential to succeed, a strong management team is essential. Highlight your key players’ backgrounds, emphasizing those skills and experiences that prove their ability to grow a company.
Ideally, you and/or your team members have direct experience in managing cybersecurity businesses. If so, highlight this experience and expertise. But also highlight any experience that you think will help your business succeed.
If your team is lacking, consider assembling an advisory board. An advisory board would include 2 to 8 individuals who would act as mentors to your business. They would help answer questions and provide strategic guidance. If needed, look for advisory board members with experience in managing a cybersecurity business or successfully running a data management business.
Financial Plan
Your financial plan should include your 5-year financial statement broken out both monthly or quarterly for the first year and then annually. Your financial statements include your income statement, balance sheet, and cash flow statements.
Income Statement
An income statement is more commonly called a Profit and Loss statement or P&L. It shows your revenue and then subtracts your costs to show whether you turned a profit or not.
In developing your income statement, you need to devise assumptions. For example, will you increase customer retention by 20% quarterly, offer reduced pricing for hardware maintenance contracts, or offer discounted packaged pricing for multiple services? And will sales grow by 2% or 10% per year? As you can imagine, your choice of assumptions will greatly impact the financial forecasts for your business. As much as possible, conduct research to try to root your assumptions in reality.
Balance Sheets
Balance sheets show your assets and liabilities. While balance sheets can include much information, try to simplify them to the key items you need to know about. For instance, if you spend $50,000 on building out your cybersecurity business, this will not give you immediate profits. Rather it is an asset that will hopefully help you generate profits for years to come. Likewise, if a lender writes you a check for $50,000, you don’t need to pay it back immediately. Rather, that is a liability you will pay back over time.
Cash Flow Statement
Your cash flow statement will help determine how much money you need to start or grow your business, and ensure you never run out of money. What most entrepreneurs and business owners don’t realize is that you can turn a profit but run out of money and go bankrupt.
When creating your Income Statement and Balance Sheets be sure to include several of the key costs needed in starting or growing a cybersecurity business:
- Cost of computer and software equipment
- Payroll or salaries paid to staff
- Business insurance
- Other start-up expenses (if you’re a new business) like legal expenses, permits, furnishings and travel expenses
Attach your full financial projections in the appendix of your plan along with any supporting documents that make your plan more compelling. For example, you might include the cybersecurity credentials of the CEO and COO or a list of client contracts.
Writing a business plan for your cybersecurity business is a worthwhile endeavor. If you follow the template above, by the time you are done, you will truly be an expert. You will understand the cybersecurity industry, your competition, and your customers. You will develop a marketing strategy and will understand what it takes to launch and grow a successful cybersecurity business.
Don’t you wish there was a faster, easier way to finish your Cybersecurity business plan?
OR, Let Us Develop Your Plan For You
Since 1999, Growthink has developed business plans for thousands of companies who have gone on to achieve tremendous success. See how a Growthink business planning consultant can create your business plan for you.
Other Helpful Business Plan Articles & Templates

Cybersecurity Business Plan Template
Written by Dave Lavinsky
Cybersecurity Business Plan
You’ve come to the right place to create your Cybersecurity business plan.
We have helped over 1,000 entrepreneurs and business owners create business plans and many have used them to start or grow their Cybersecurity businesses.
Below is a template to help you create each section of your Cybersecurity business plan.
Executive Summary
Business overview.
The Cyber Guardian business is a startup cybersecurity company located in Burlingame, California. The company was founded by Lynn Frederick, who has a fifteen-year history working in the cybersecurity industry, in increasingly responsible roles. This expertise positions him to start and effectively grow a successful cybersecurity company. Lynn believes his coding and managerial experience, coupled with a deep knowledge of cybersecurity practices will provide everything needed for long-term growth and profitability.
Cyber Guardian is a cutting-edge cybersecurity startup dedicated to providing robust cybersecurity solutions to small and medium enterprises (SMEs). Founded by cybersecurity expert Lynn Frederick, Cyber Guardian leverages advanced technologies and deep industry experience to protect clients’ digital assets.
Product Offering
The following are the services that Cyber Guardian will provide:
- Vulnerability Assessment
- Managed Security Services
- Incident Response
- Cybersecurity Training & Awareness
Customer Focus
The primary customers of Cyber Guardian are SMEs across various sectors such as finance, healthcare, and retail, which are increasingly vulnerable to cyber threats but often lack the resources to maintain a full-fledged internal cybersecurity team.
Management Team
Cyber Guardian is owned and operated by Lynn Frederick, who graduated from UC Berkely with a bachelor’s degree in Software Security. Since his graduation, Lynn has been working at a large cybersecurity company in increasingly responsible roles. Lynn’s knowledge, skill, and customer service orientation prompted several customers to encourage him to launch his own company, stating they trust him above all others, and would follow him to the new firm. As he considered starting his own company, Lynn began securing contracts from these clients, ensuring they will follow him to Cyber Guardian when the company fully launches.
Lynn Frederick has recruited Gloria Perlman, who also attended UC Berkeley, to be the Administrative Manager in the new company. In this role, Gloria will oversee and direct staff members in the execution of the company vision, as well as run the back office operation and bookkeeping.
Success Factors
Cyber Guardian will be able to achieve success by offering the following competitive advantages:
- Friendly, knowledgeable, and highly-qualified team of IT professionals
- Services that leverage cutting-edge technology and techniques for maintaining security
- Cyber Guardian offers the best pricing in town, with a comparatively cost effective pricing structure.
Financial Highlights
Cyber Guardian is seeking $175,000 in debt financing to launch its cybersecurity operation. The funding will be dedicated toward securing the office space and purchasing technology and setting up the necessary infrastructure. Funding will also be dedicated toward three months of overhead costs to include payroll of the staff, rent, and marketing costs for the print ads and marketing costs. The breakout of the funding is below:
- Office space build-out: $10,000
- Technology and infrastructure: $50,000
- Three months of overhead expenses (payroll, rent, utilities): $100,000
- Marketing costs: $5,000
- Working capital: $10,000
The following graph outlines the financial projections for Cyber Guardian.
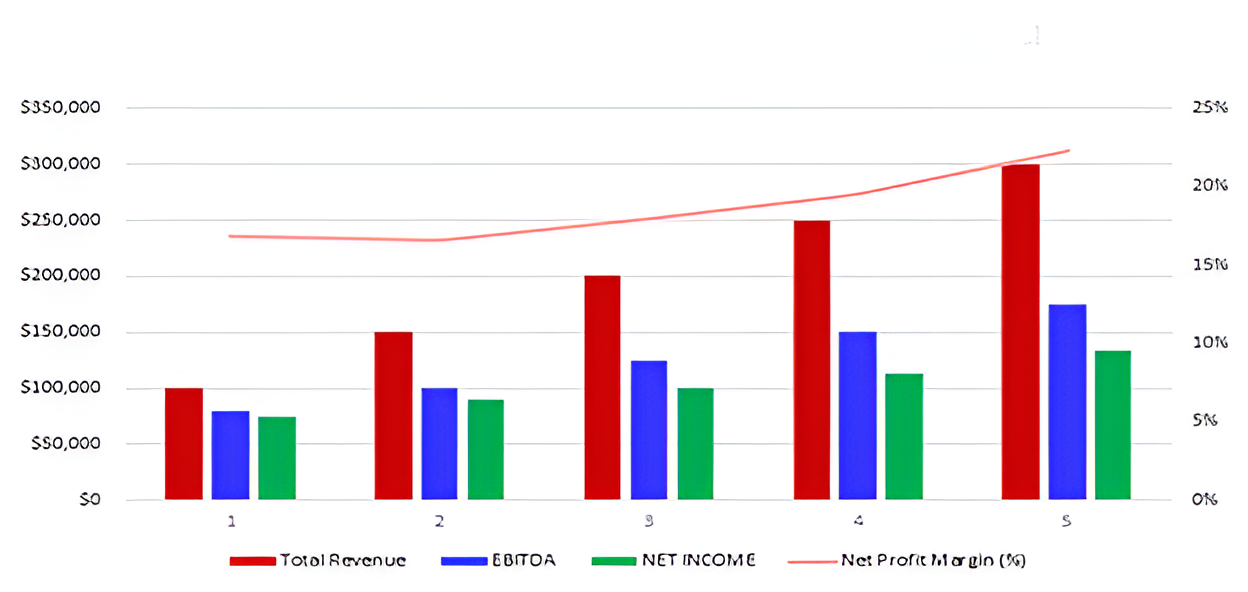
Company Overview
Who is cyber guardian.
Cyber Guardian is a newly established, full-service cybersecurity company in Burlingame, California. Cyber Guardian will be the most reliable, cost-effective, and efficient cybersecurity choice in the city and the surrounding communities. Cyber Guardian will provide a tailored menu of cybersecurity solutions designed to protect SMEs from the growing threats of cyberattacks, ensuring business continuity and regulatory compliance.
Lynn Frederick will serve as manager and mentor to each of his team members, all of whom are highly qualified in their own right, and experienced in the most important aspects of cybersecurity. Cyber Guardian offers peace of mind for all its clients and ensures all issues are taken care of expeditiously while delivering the best customer service.
Cyber Guardian History
Cyber Guardian is owned and operated by Lynn Frederick. As a former cybersecurity manager for several years, he developed a unique capability to design and implement cybersecurity solutions that clearly reflect his skills and abilities. The company is built on the foundation of its founder’s extensive industry expertise and a deep understanding of the cybersecurity challenges faced by SMEs. Furthermore, Lynn Frederick has gained the trust and commitment of several clients in advance of opening his business and has begun to sign contracts with each to provide tailored cybersecurity solutions once the company launches.
Since incorporation, Cyber Guardian has achieved the following milestones:
- Registered Cyber Guardian, LLC to transact business in the state of California.
- Has a contract in place for a 10,000 square foot office at one of the midtown buildings
- Reached out to numerous contacts to include Cyber Guardian in upcoming advertising and marketing programs.
- Began recruiting a staff of experienced IT professionals to work at Cyber Guardian
Cyber Guardian Services
Cyber Guardian offers end-to-end security services, from risk assessments and monitoring to incident response and recovery, alongside continuous updates and training to cope with evolving threats.
The following will be the services Cyber Guardian will provide:
- Performance reports and analytics: weekly reports to clients
- Superior day to day client management
Industry Analysis
The cybersecurity market is growing due to increasing internet penetration, a surge in cybercrime, and stringent regulatory requirements. The demand for cybersecurity solutions is expected to rise, especially among SMEs, which are typically less well-protected.
The cybersecurity industry is expected to reach $78.3 billion this year, and continue to grow at an annual rate of 7.7% over the next five years.
Cybersecurity is becoming increasingly important, as companies, governments, and individuals are more and more reliant on IT systems, which are vulnerable to malicious actions. This digital transformation has made security a priority for organizations of every size.
The cybersecurity software industry is growing due to increasing threats of hacking and malware. Rising sales, limited costs and a reliance on skilled labor have contributed to strong profits. Developers invest heavily in research and development to stay ahead of the game. Purchases costs vary depending on the developer, but are diminishing as cloud computing limits the need for hardware.
Customer Analysis
Demographic profile of target market.
Cyber Guardian will target companies that currently utilize cybersecurity and those that have a need for cybersecurity in Burlingame, California and, in the greater San Francisco region. The company will target small-to-medium sized businesses who have not yet acquired cybersecurity, as well as larger corporations without an effective cybersecurity solution.
Customer Segmentation
Cyber Guardian will primarily target the following customer profiles in the Bay Area:
- Finance SMEs: High-value transactions and regulatory compliance needs.
- Healthcare SMEs: Require protection of sensitive patient data.
- Retail SMEs: Need to secure consumer data and e-commerce platforms.
Competitive Analysis
Direct and indirect competitors.
Cyber Guardian will face competition from other companies with similar business profiles. A description of each competitor company is below.
IT Partners
Established in 2000, IT Partners is an IT managed services company that provides managed IT services throughout North America. IT Partners is equipped to offer a comprehensive range of IT solutions for businesses of all sizes. Solutions include cloud computing solutions, cybersecurity defense, network design and implementation, critical incident response, and 24/7 help desk support. The company uses a proactive approach to focus on prevention and designs customized strategies tailored to each client’s specific requirements and goals. IT Partners has over 250 IT professionals on its team and has served over 1,900 businesses. The company provides solutions for various industries, including accounting, architecture, engineering, construction, education, finance, healthcare, hospitality, insurance, legal, manufacturing, retail, recruiting/staffing, real estate, and non-profits.
Service Offerings Include:
- Managed IT Services
- Internal IT Support
- Virtual CIO
- Network Management
- Cybersecurity Protection
- Backup Monitoring/Remediation
- Device Management
- Patch Management
- Cloud Solutions
- Delmiaworks Support (IQMS)
- Amazon Web Services (AWS Cloud services, AWS Cloud migration, AWS managed cloud, AWS application modernization, AWS serverless architecture)
Bay Area Technology Solutions
Established in 1996, Bay Area Technology Solutions (BATS) is an IT services company that specializes in IT support and cybersecurity solutions for Bay Area businesses. BATS employs a team of highly credentialed technology professionals with expertise in a wide range of services, from remote help desk to on-site support, storage, server consolidation, virtualization, wireless, business continuity, archiving, POS systems, cybersecurity, and data center builds.
- Cybersecurity Services
- Application Support & Development
- Voice over IP (VoIP) Services
Miklos Technologies
Established in 1997, Miklos Technologies (Miklos IT) is a managed IT services company that serves businesses throughout the United States. Miklos IT supports numerous industries, including healthcare, logistics, finance, professional services, manufacturing, real estate, retail, ecommerce, construction, engineering, architecture, legal, private equity, education, non-profit, science, hospitality, and entertainment companies. Miklos IT provides four key service areas: technology consulting, IT, software, and marketing. The company offers business and technology consulting in various areas such as business transformation, growth & strategy planning, IT regulation compliances, mergers & acquisitions, technology risk assessments, operations, marketing brand strategy, sales, and recruiting & staffing.
- Managed IT Services & Security
- Software Development
- Ecommerce & Custom Websites
- Digital Marketing
- IT Consulting
- Support & Advance Custom Software
- Cybersecurity
- Systems Integration
- Cloud Computing & Migrations
Competitive Advantage
Cyber Guardian will be able to offer the following advantages over their competition:
- Friendly, knowledgeable, and highly-qualified team of experienced IT professionals
- Comprehensive menu of personalized, SME-focused solutions
- Cyber Guardian offers flexible pricing models designed to cater to the specific needs of smaller businesses.
Marketing Plan
Brand & value proposition.
Cyber Guardian will offer a unique value proposition to its clientele:
- Highly-qualified team of skilled employees who are able to provide a comprehensive cybersecurity program that brings peace of mind to their clients
- Experience with keeping abreast of evolving threats and security issues
- Flexible pricing models
Promotions Strategy
The promotions strategy for Cyber Guardian is as follows:
Word of Mouth/Referrals
The founder of Cyber Guardian has built an extensive list of contacts over the years by providing exceptional service and highly skilled and effective cybersecurity services. Many of these contacts and clients will follow the founder to the new company and help spread the word of Cyber Guardian.
Professional Associations and Networking
Industry associations and local networking will become a top priority for the team at Cyber Guardian. The management team will seek active leadership roles, which will expand its credibility within the industry.
Social Media Marketing
Cyber Guardian will focus primarily on marketing its services and on maximizing relationship opportunities via social media efforts.
Website/SEO Marketing
Cyber Guardian’s website will be well organized, informative, and list all the services that Cyber Guardian provides. Further, the company will engage in SEO marketing tactics so that anytime someone searches online for “cybersecurity company” or “cybersecurity company near me,” Cyber Guardian will be listed at the top of the search results.
Operations Plan
The following will be the operations plan for Cyber Guardian. Operation Functions:
- Lynn Frederick will be the owner and President of the company. He will manage client relations. Lynn Frederick has spent the past year recruiting the following staff:
- Gloria Perlman will be the Administrative Manager, and will oversee and direct staff members in the execution of the company vision, as well as run the back office operation and bookkeeping.

Milestones:
Cyber Guardian will have the following milestones completed in the next six months.
- 5/1/202X – Finalize contract to lease office space
- 5/15/202X – Finalize personnel and staff employment contracts for Cyber Guardian
- 6/1/202X – Finalize contracts for Cyber Guardian clients
- 6/15/202X – Begin networking at industry events
- 6/22/202X – Begin moving into Cyber Guardian office
- 7/1/202X – Cyber Guardian opens its doors for business
Financial Plan
Key revenue & costs.
The revenue drivers for Cyber Guardian are the fees charged for deployed solutions. Strong growth and a recurring revenue model, with client bases growing to generate a consistent revenue stream, also support profitability.
The cost drivers will be the overhead costs required to staff Cyber Guardian. The expenses will be the payroll cost, rent, utilities, technology and software costs.
Funding Requirements and Use of Funds
Key assumptions.
The following outlines the key assumptions required achieve the revenue and cost numbers in the financials and in order to pay off the startup business loan.
- Number of clients Per Month: 20
- Average revenue per Month: $200,000
- Office Lease per Year: $100,000
Financial Projections
Income statement, balance sheet, cash flow statement, cybersecurity business plan faqs, what is a cybersecurity business plan.
A cybersecurity business plan is a plan to start and/or grow your cybersecurity business. Among other things, it outlines your business concept, identifies your target customers, presents your marketing plan and details your financial projections. You can easily complete your Cybersecurity business plan using our Cybersecurity Business Plan Template here .
What are the Main Types of Cybersecurity Businesses?
There are a number of different kinds of cybersecurity businesses, some examples include: Remote security center services, Cloud security services, Vulnerability scan & management, and Endpoint security services.
How Do You Get Funding for Your Cybersecurity Business Plan?
Cybersecurity businesses are often funded through small business loans. Personal savings, credit card financing and angel investors are also popular forms of funding.
What are the Steps To Start a Cybersecurity Business?
Starting a cybersecurity business can be an exciting endeavor. Having a clear roadmap of the steps to start a business will help you stay focused on your goals and get started faster. 1. Develop A Cybersecurity Business Plan - The first step in starting a business is to create a detailed cybersecurity business plan that outlines all aspects of the venture. This should include potential market size and target customers, the services or products you will offer, pricing strategies and a detailed financial forecast. 2. Choose Your Legal Structure - It's important to select an appropriate legal entity for your cybersecurity business. This could be a limited liability company (LLC), corporation, partnership, or sole proprietorship. Each type has its own benefits and drawbacks so it’s important to do research and choose wisely so that your cybersecurity business is in compliance with local laws. 3. Register Your Cybersecurity Business - Once you have chosen a legal structure, the next step is to register your cybersecurity business with the government or state where you’re operating from. This includes obtaining licenses and permits as required by federal, state, and local laws. 4. Identify Financing Options - It’s likely that you’ll need some capital to start your cybersecurity business, so take some time to identify what financing options are available such as bank loans, investor funding, grants, or crowdfunding platforms. 5. Choose a Location - Whether you plan on operating out of a physical location or not, you should always have an idea of where you’ll be based should it become necessary in the future as well as what kind of space would be suitable for your operations. 6. Hire Employees - There are several ways to find qualified employees including job boards like LinkedIn or Indeed as well as hiring agencies if needed – depending on what type of employees you need it might also be more effective to reach out directly through networking events. 7. Acquire Necessary Cybersecurity Equipment & Supplies - In order to start your cybersecurity business, you'll need to purchase all of the necessary equipment and supplies to run a successful operation. 8. Market & Promote Your Business - Once you have all the necessary pieces in place, it’s time to start promoting and marketing your cybersecurity business. This includes creating a website, utilizing social media platforms like Facebook or Twitter, and having an effective Search Engine Optimization (SEO) strategy. You should also consider traditional marketing techniques such as radio or print advertising.
Cyber Insight
How to Craft a Strong Cyber Security Business Plan: A Step-by-Step Guide
Updated on: June 17, 2023

You’re sitting at your desk, staring at a blank page with a daunting task ahead – crafting a strong cyber security business plan. Your mind is racing with questions and doubts. Where do you even start? What are the crucial elements to include? How do you ensure you’re covering everything you need to? Take a deep breath, because you’re in the right place. As a cyber security expert with years of experience under my belt, I’ve been through this process plenty of times. In fact, I’ve learned a few things along the way that can help take your plan from mediocre to exceptional. In this step-by-step guide, I’ll help you craft a business plan that will not only impress investors but will also give your company a solid foundation to stand on. So, let’s dive in.
How do I write a cyber security business plan?
my company specializes in providing comprehensive security solutions to companies of all sizes. Our services include network security, data protection, threat assessment, and incident response.
Our direct competitors include established cyber security companies such as Symantec, McAfee, and Cisco. However, we position ourselves as a more personalized and cost-effective option for small to medium-sized businesses without compromising on the quality of our services.
We target companies across various industries, including finance, healthcare, and retail. Our ideal customers are businesses without an in-house IT security team or those looking to outsource their security needs to the experts.
Our marketing plan includes various initiatives such as targeted online advertisements, search engine optimization, and content marketing. We also plan to attend industry conferences and events to connect with potential clients and network with other cyber security professionals.
Our financial strategy is to start with moderate pricing to acquire new clients and gradually increase it over time as our reputation and customer base grow. We plan to reinvest in the business by hiring more experienced professionals and investing in advanced security technologies to stay ahead of the competition.
- Overview of Industry of cyber security
- Type of cyber security company operated
- Details of direct competitors
- Overview of the target customers
- Marketing plan overview
- Financial strategy overview
???? Pro Tips:
1. Understand the market: Research the cyber security industry and identify the services that are in high demand. Determine which niche you want to target and how your business will fit in.
2. Identify your target audience: Decide who your potential customers are and what they need. Develop a detailed customer profile including demographics, job titles, behaviors, and pain points.
3. Conduct a SWOT analysis: Identify the strengths, weaknesses, opportunities, and threats of your business. Analyze your competition and determine how you can stand out in the market.
4. Determine your business model: Decide on the services you will offer and how you will deliver them. Determine your pricing strategy, revenue streams, and cost structure.
5. Develop a marketing strategy: Develop a comprehensive marketing plan to reach your target audience. Utilize various channels such as social media, email marketing, content marketing, and paid advertising to promote your cyber security business.
Introduction to the Cyber Security Industry
The world we live in today is largely dependent on technology, and with that comes the need for cybersecurity. The increased use of technology has increased the vulnerability of businesses and individuals to cyber threats such as malware and hacking. This has led to a growing demand for cybersecurity services in recent years. The cyber security industry is an ever-growing and constantly evolving field, with advancements in technology constantly giving rise to new cyber threats that must be addressed.
According to industry reports, the global cybersecurity market size is expected to reach USD 248.26 billion by 2023, growing at a compound annual growth rate (CAGR) of 10.2% during the forecast period. This growth is largely driven by the increasing number of cyber attacks and data breaches, as well as the need for organizations to comply with stringent data protection regulations.
Description of Your Cyber Security Business
my business entails offering comprehensive security solutions to businesses and individuals. Our range of services includes threat analysis and prevention, incident response, network security, cloud security, security audits and vulnerability assessments. Our team consists of highly skilled professionals with years of experience in the field of cybersecurity.
Our approach is to provide customized cybersecurity solutions to our clients based on their unique needs and requirements. We understand the importance of staying up-to-date with the latest trends and technologies in the industry, which is why we constantly invest in research and development, and innovative security solutions.
Analysis of Direct Competitors in Your Field
There are several direct competitors in the cybersecurity industry that offer similar services as ours. Some of the more well-known players include IBM, Symantec, McAfee, and Cisco Systems. These companies are known for their comprehensive security solutions and have a large market share, which poses a challenge for new entrants like us.
To differentiate ourselves from our competitors, we focus on providing tailored solutions to our clients, which takes into consideration their unique needs and requirements. We also emphasize on our speed of response and personalized service, ensuring that our clients receive quick and efficient service. By differentiating ourselves in this way, we believe we can carve out a niche market for ourselves despite the competition.
Identifying and Understanding Your Target Customers
Our primary target customers include small to medium-sized businesses, start-ups, and individuals who operate in a digital environment. We provide security solutions to businesses in a variety of industries including healthcare, finance, and education. We understand that these businesses face unique risks and challenges, which is why we offer a personalized approach to security solutions that are tailored to their needs.
Our individual clients include those who are concerned about online privacy and security. We offer services such as VPN solutions, password management, and identity theft protection. We also provide security training to individuals such as how to identify phishing emails and tips on how to protect sensitive information.
Outlining Your Marketing Strategy
Our marketing strategy focuses on leveraging online channels such as social media and content marketing. We will create targeted content that speaks directly to the needs of our target audience. Additionally, we will use SEO techniques to increase our online visibility and drive traffic to our website. We will also attend industry conferences and trade shows to build relationships with potential clients.
We plan to offer freemium versions of our security products to generate leads, as well as offer referral programs for existing clients to generate new business. Finally, we will leverage word-of-mouth marketing by encouraging our satisfied clients to share their positive experiences with others.
Financial Plan and Projections for Your Business
Our financial plan includes start-up costs, which will include licensing fees, hiring employees, and developing a marketing strategy. We project our monthly revenue to be $50,000 in the first year, with a net profit of 20%. We will reinvest our profits in marketing efforts, research and development and expanding our workforce.
As we grow and establish ourselves in the industry, we plan to offer additional security services such as penetration testing and security compliance consulting. We estimate that our revenue will grow at a CAGR of 15% in the second and third years, with a net profit margin of 25%.
Conclusion and Next Steps
In conclusion, the cybersecurity industry is a growth market that presents opportunities for new players to enter. Despite having several direct competitors, our customized approach to security solutions and emphasis on personalized service will set us apart in the market.
Our next steps include implementing our marketing strategy, establishing relationships with potential clients, and investing in research and development to stay ahead of the curve in the ever-evolving industry. With a strong team and a commitment to meeting the unique needs of our clients, we believe we can thrive in this industry and make a significant impact on the cybersecurity landscape.
most recent

Cybersecurity Basics
What are the three approaches to security in cyber security: explained.

Services & Solutions
What is security solution and why it matters: ultimate guide.

Training & Certification
Is a masters in cybersecurity worth the investment.

What is the Cyber Security Strategy Objective? Protecting Against Breaches.

What is Dart in Cyber Security? A Powerful Tool for Threat Detection.

Decoding SLED: Is Public Sector Cybersecurity the Same?
PH +1 000 000 0000
24 M Drive East Hampton, NY 11937
© 2024 INFO
- Sample Business Plans
- IT, Staffing & Customer Service
Cyber Security Business Plan
If you are planning to start a new business in the cybersecurity space, the first thing you will need is a business plan. Use our sample cyber security business plan created using upmetrics business plan software to start writing your business plan in no time.
Before you start writing your business plan for your new cybersecurity business, spend as much time as you can reading through some examples of software-related business plans .
Reading sample business plans will give you a good idea of what you’re aiming for and also it will show you the different sections that different entrepreneurs include and the language they use to write about themselves and their business plans.
We have created this sample cyber security business plan for you to get a good idea about what a perfect business plan should look like and what details you will need to include in your stunning business plan.
Cyber Security Business Plan Outline
This is the standard cyber security business plan outline which will cover all important sections that you should include in your business plan.
- The Business
- 3 Year profit forecast
- Company Owner
- Why the business is being started?
- Startup cost
- Startup Requirements
- Products and Services
- Market Trends
- Marketing Share
- Institutions & Organizations
- Celebrities & Individuals
- Business Target
- Product Pricing
- Competitive Analysis
- Sales Monthly
- Sales Yearly
- Sales Forecast
- Company Staff
- Average Salary of Employees
- Important Assumptions
- Brake-even Analysis
- Profit Yearly
- Gross Margin Yearly
- Projected Cash Flow
- Projected Balance Sheet
- Business Ratios
Say goodbye to boring templates
Build your business plan faster and easier with AI
Plans starting from $7/month

After getting started with upmetrics , you can copy this sample business plan into your business plan and modify the required information and download your cyber security business plan pdf and doc file . It’s the fastest and easiest way to start writing your business plan.
Download a sample cyber security business plan
Need help writing your business plan from scratch? Here you go; download our free cyber security business plan pdf to start.
It’s a modern business plan template specifically designed for your cyber security business. Use the example business plan as a guide for writing your own.
Related Posts
IT Consulting Business Plan
SaaS Business Plan
Customer Analysis writing Guide
How to create a Compelling Business Plan
Digital Marketing Agency Business Plan
Software Company Business Plan
About the Author
Upmetrics Team
Upmetrics is the #1 business planning software that helps entrepreneurs and business owners create investment-ready business plans using AI. We regularly share business planning insights on our blog. Check out the Upmetrics blog for such interesting reads. Read more
Turn your business idea into a solid business plan
Explore Plan Builder
Plan your business in the shortest time possible
No Risk – Cancel at Any Time – 15 Day Money Back Guarantee

Create a great Business Plan with great price.
- 400+ Business plan templates & examples
- AI Assistance & step by step guidance
- 4.8 Star rating on Trustpilot
Streamline your business planning process with Upmetrics .


Crafting a Cybersecurity Business Plan: Key Considerations for Success

Cyber Security Company Bundle
Embarking on a cybersecurity venture requires meticulous planning and preparation. Before crafting a comprehensive business plan, savvy entrepreneurs must navigate a 9-step checklist to ensure their venture is poised for success. From conducting in-depth market research to assembling a skilled cybersecurity team , this introductory guide outlines the essential steps that will lay the foundation for a thriving cybersecurity business.
Steps Prior To Business Plan Writing
Before embarking on the journey of writing a comprehensive business plan for a cybersecurity venture, it is crucial to lay the groundwork and address several key considerations. This checklist outlines the essential steps to be taken to ensure a well-informed and strategically-aligned plan.
Conduct Thorough Market Research on the Cybersecurity Industry
Embarking on a cybersecurity business venture requires a deep understanding of the industry landscape. Conducting comprehensive market research is a crucial first step in developing a robust business plan for your Cyber Security startup, ShieldSecure Consulting .
Begin by analyzing the overall cybersecurity industry trends . According to a recent report by MarketsandMarkets, the global cybersecurity market is expected to grow from $167.13 billion in 2020 to $281.74 billion by 2025 , at a CAGR of 11.0% during the forecast period. This rapid growth is driven by the increasing number of cyber threats, the need for robust data protection, and the rising adoption of cloud-based technologies.
- Closely monitor industry publications, news outlets, and research reports to stay updated on the latest cybersecurity trends, threats, and market dynamics.
- Attend industry events, conferences, and webinars to network with industry professionals and gain insights into the evolving cybersecurity landscape.
Next, delve deeper into your target market - small to medium-sized businesses (SMBs). According to a study by the National Cyber Security Centre, 43% of cyber attacks target small businesses , yet many lack the resources and expertise to effectively protect themselves. This presents a significant opportunity for your Cyber Security startup, ShieldSecure Consulting , to provide cost-effective, customized cybersecurity solutions to this underserved market segment.
Analyze the pain points experienced by SMBs in the cybersecurity domain. Common challenges include a lack of in-house IT expertise, limited budgets, and the complexity of implementing and maintaining effective security measures. By addressing these specific needs, you can position ShieldSecure Consulting as a trusted partner that delivers tailored solutions to help SMBs safeguard their operations.
- Conduct customer interviews, surveys, and focus groups to gain a deeper understanding of the specific cybersecurity challenges faced by your target market.
- Analyze industry reports and case studies to identify common pain points and unmet needs within the SMB cybersecurity landscape.
Finally, examine the competitive landscape of the cybersecurity industry. Identify the key players, their service offerings, pricing strategies, and unique value propositions. Assess how ShieldSecure Consulting can differentiate itself and carve out a competitive advantage in the market. This analysis will inform the development of your service portfolio, pricing structure, and overall strategic positioning.
- Utilize online tools and industry databases to research and benchmark your competitors' offerings, pricing, and market share.
- Conduct a SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis to identify your startup's unique strengths and opportunities to outperform competitors.
By conducting thorough market research on the cybersecurity industry, you will gain invaluable insights to inform the development of your Cyber Security business plan and positioning strategy for ShieldSecure Consulting . This foundational work will set the stage for the subsequent steps in your entrepreneurial journey.
Identify Target Market and Customer Pain Points
As you embark on your cybersecurity business venture, it is crucial to thoroughly understand your target market and the specific pain points your customers are facing. This knowledge will serve as the foundation for developing a tailored and effective cybersecurity solution that addresses their unique needs.
To identify your target market, begin by analyzing industry trends and the competitive landscape. Examine the cybersecurity challenges faced by small to medium-sized businesses (SMBs), as this segment often lacks the resources and expertise to effectively safeguard their digital assets. According to a recent industry report, SMBs account for 43% of all cyberattacks, yet only 14% have a formal cybersecurity incident response plan in place.
Next, delve deeper into the specific pain points experienced by your target customers. Common pain points in the cybersecurity domain may include:
- Lack of in-house cybersecurity expertise to implement and maintain robust security measures
- Insufficient budget to invest in comprehensive cybersecurity solutions
- Complexity in navigating the evolving cybersecurity landscape and compliance requirements
- Concerns about data breaches and the potential impact on business operations and reputation
- Difficulty in keeping up with the latest cybersecurity threats and best practices
- Conduct in-depth interviews with potential customers to gain a deeper understanding of their specific cybersecurity challenges and concerns.
- Analyze industry reports and market research to identify emerging trends and pain points within your target market.
- Engage with industry associations or online communities to gather insights from SMB owners and decision-makers.
By thoroughly understanding your target market and their pain points, you can develop a cybersecurity service portfolio that addresses their unique needs and positions your business as a trusted partner in safeguarding their digital assets. This customer-centric approach will be instrumental in driving the success of your cybersecurity venture.
Analyze Competitor Offerings and Pricing Strategies
As ShieldSecure Consulting prepares to launch its cybersecurity services, it's crucial to thoroughly analyze the competitive landscape. By understanding the offerings and pricing strategies of key players in the industry, ShieldSecure can position itself as a unique and valuable solution for its target market of small to medium-sized businesses (SMBs).
The cybersecurity market is rapidly evolving, with a wide range of service providers catering to businesses of all sizes. According to a recent industry report, the global cybersecurity market is expected to grow at a CAGR of 12.5% from 2021 to 2028, reaching a value of $345.4 billion by 2028 . This growth is driven by the increasing adoption of cloud computing, the proliferation of connected devices, and the growing awareness of the importance of robust cybersecurity measures.
When analyzing ShieldSecure's competitors, it's essential to consider the range of services they offer, their pricing structures, and their unique value propositions. A survey of 50 cybersecurity service providers in the SMB market revealed that the average monthly cost for a comprehensive cybersecurity package ranges from $500 to $2,000 per month, depending on the size and complexity of the business . However, many of these offerings are standardized and may not be tailored to the specific needs of individual SMBs.
- Identify the key players in the cybersecurity industry that are targeting the SMB market, and analyze their service offerings, pricing, and unique value propositions.
- Conduct a thorough review of industry reports and market research to understand the current trends, pricing benchmarks, and competitive dynamics in the cybersecurity sector.
- Engage with potential customers to understand their specific pain points, budget constraints, and preferences when it comes to cybersecurity solutions.
By carefully analyzing the competitive landscape, ShieldSecure can develop a unique value proposition that sets it apart from its competitors. For example, ShieldSecure may offer a more personalized and flexible approach to cybersecurity, with customized solutions that address the specific needs of each SMB client at a competitive price point . This level of customization and customer-centric focus can be a powerful differentiator in a crowded market.
Determine Unique Value Proposition and Competitive Advantages
In the highly competitive cybersecurity landscape, it is essential for ShieldSecure Consulting to develop a strong and differentiated value proposition that sets it apart from its competitors. By clearly articulating the unique benefits and advantages that ShieldSecure offers, the company can effectively position itself in the market and attract its target customers.
To determine ShieldSecure's unique value proposition, the company should start by conducting a thorough analysis of the cybersecurity industry and its competitive landscape. This includes researching the service offerings, pricing structures, and positioning of major players in the market , as well as identifying any gaps or unmet needs that ShieldSecure can address.
- Leverage industry reports and market research to gain a comprehensive understanding of the cybersecurity landscape.
- Engage with potential customers to understand their specific pain points and challenges, and how ShieldSecure can provide tailored solutions.
- Analyze the strengths and weaknesses of your competitors, and identify opportunities where ShieldSecure can differentiate itself.
Based on this analysis, ShieldSecure should develop a unique value proposition that clearly communicates the key benefits it offers to its target customers. This may include factors such as specialized expertise, personalized service, cost-effectiveness, or innovative technology . By positioning itself as a trusted partner that can provide comprehensive and customized cybersecurity solutions, ShieldSecure can create a strong competitive advantage in the market.
To further enhance its competitive edge, ShieldSecure should also consider developing strategic partnerships with complementary service providers or technology vendors. These alliances can help the company expand its service offerings, leverage complementary capabilities, and gain access to a broader customer base.
- Identify potential partners that can enhance your service portfolio or provide access to new markets.
- Establish clear collaboration agreements and revenue-sharing models to ensure mutually beneficial partnerships.
- Continuously monitor and adapt your value proposition and competitive strategy as the cybersecurity landscape evolves.
By focusing on developing a unique and compelling value proposition, and leveraging strategic partnerships, ShieldSecure Consulting can position itself as a leading provider of cybersecurity services for small and medium-sized businesses. This strategic approach will be crucial in helping the company stand out in the crowded cybersecurity market and attract its target customers.
Assess financial requirements and potential funding sources
Determining the financial requirements for a cybersecurity startup is a critical step in the business planning process. Entrepreneurs must carefully examine the capital needed to cover initial setup costs, ongoing operational expenses, and any necessary investments in technology, infrastructure, and talent. According to a recent industry report, the average startup cost for a cybersecurity firm ranges from $ 50,000 to $250,000 , depending on the scope of services and the size of the target market.
Once the financial requirements have been established, cybersecurity entrepreneurs must explore potential funding sources to support their venture. A survey by the National Venture Capital Association found that 45% of cybersecurity startups secured their initial funding through angel investors, 30% through venture capital firms, and 25% through personal savings or loans. Exploring a mix of these options can help entrepreneurs access the necessary capital to launch and grow their cybersecurity business.
- Carefully research and compare different funding sources, such as angel investors, venture capitalists, and government grants, to find the best fit for your cybersecurity startup.
- Develop a detailed financial plan that outlines your startup's capital requirements, operating expenses, and revenue projections to strengthen your funding proposals.
- Consider exploring alternative financing options, such as crowdfunding platforms or small business loans, to diversify your funding sources and reduce reliance on a single source of capital.
In addition to identifying the initial funding requirements, cybersecurity entrepreneurs must also plan for ongoing financial management and growth. Industry data suggests that successful cybersecurity startups typically reinvest 30% to 50% of their revenue into research and development, technology upgrades, and talent acquisition to maintain a competitive edge. Developing a robust financial strategy and maintaining a strong financial position will be crucial for the long-term success and sustainability of the cybersecurity business.
Develop a Detailed Service Portfolio and Pricing Structure
At the core of ShieldSecure's cybersecurity offerings is a comprehensive service portfolio that caters to the diverse needs of small and medium-sized businesses. By carefully curating a range of solutions, the company aims to provide its clients with a one-stop-shop for all their cybersecurity requirements.
ShieldSecure's service portfolio includes vulnerability assessments , penetration testing , incident response planning , security awareness training , and managed security services . These services are designed to address the common pain points experienced by SMEs, such as limited in-house IT resources, lack of cybersecurity expertise, and the need for cost-effective security solutions.
- Regularly review and update the service portfolio to align with evolving industry trends and client needs.
- Offer flexible service packages that allow clients to customize their cybersecurity solutions based on their specific requirements and budget.
- Emphasize the value-added benefits of each service, such as reduced risk, improved compliance, and enhanced business resilience.
Crafting a pricing structure that balances affordability and profitability is crucial for the success of ShieldSecure's cybersecurity business. The company has carefully analyzed the market rates for similar services, as well as the financial constraints faced by its target SME clientele.
ShieldSecure's pricing model features a combination of fixed-fee and subscription-based offerings. The fixed-fee services, such as vulnerability assessments and penetration testing, provide clients with a clear and predictable cost structure. The subscription-based services, including managed security and security awareness training, offer a more scalable and cost-effective solution for ongoing cybersecurity needs.
- Regularly benchmark the pricing against industry standards and competitors to ensure competitive positioning.
- Offer flexible payment terms, such as monthly or annual subscriptions, to accommodate the budgetary preferences of SME clients.
- Explore bundled service packages that provide discounted pricing for clients who opt for multiple cybersecurity solutions.
By developing a robust service portfolio and a strategic pricing structure, ShieldSecure aims to establish itself as a trusted partner in the cybersecurity landscape for small and medium-sized businesses. This comprehensive approach not only addresses the unique security challenges faced by SMEs but also positions the company for sustainable growth and profitability in the rapidly evolving cybersecurity market.
Establish Key Partnerships and Strategic Alliances
In the competitive cybersecurity landscape, forging strategic partnerships and alliances can be a game-changer for a startup like ShieldSecure Consulting. By tapping into the expertise, resources, and customer networks of established industry players, ShieldSecure can accelerate its growth, enhance its service offerings, and gain a competitive edge.
One of the key priorities for ShieldSecure should be to identify and cultivate relationships with managed service providers (MSPs) and IT service firms that cater to small and medium-sized businesses. These partnerships can provide ShieldSecure with a ready-made customer base, as well as opportunities to integrate its cybersecurity solutions into the service offerings of its partners.
- Aim to establish strategic alliances with at least 5-10 MSPs and IT service providers within the first year of operation to gain access to a wider customer network.
- Offer co-branding and revenue-sharing opportunities to incentivize partners and foster long-term collaboration.
- Ensure seamless integration of ShieldSecure's cybersecurity solutions with the existing technology stacks and workflows of partner organizations.
Additionally, ShieldSecure should explore opportunities to forge partnerships with industry associations, cybersecurity training providers, and technology vendors. These alliances can help the company stay abreast of the latest industry trends, access specialized expertise, and tap into new customer segments.
- Aim to establish partnerships with at least 3-5 industry associations, training providers, and technology vendors within the first 18 months of operation.
- Leverage these partnerships to enhance ShieldSecure's service portfolio, optimize its cybersecurity solutions, and gain industry-wide recognition .
- Explore co-marketing and joint-venture opportunities with these partners to amplify the company's reach and visibility.
By strategically building a robust partner ecosystem, ShieldSecure can not only bolster its own capabilities but also position itself as a trusted and well-connected cybersecurity provider in the eyes of its target customers. This collaborative approach can be a crucial differentiator in a highly competitive market, helping the company expand its reach, enhance its service quality, and drive sustainable growth.
Outline Operational Processes and Resource Requirements
Establishing robust operational processes and securing the necessary resources are critical steps in building a successful cybersecurity business like ShieldSecure Consulting . By meticulously planning these aspects, entrepreneurs can ensure their business is well-equipped to deliver high-quality cybersecurity services and effectively meet the evolving needs of their target market.
One of the key operational considerations for a cybersecurity startup is the development of standardized service delivery processes . This involves mapping out the end-to-end workflow, from initial client onboarding to ongoing support and maintenance. This may include processes for threat assessments, vulnerability testing, incident response planning, and regular security monitoring and reporting.
- Leverage industry best practices and frameworks, such as NIST Cybersecurity Framework or ISO 27001, to ensure comprehensive and compliant service delivery processes.
- Implement robust quality assurance and quality control measures to maintain consistently high standards of service and client satisfaction.
Another crucial aspect is resource planning and allocation . This encompasses identifying the necessary human resources, technology infrastructure, and other assets required to execute the business's service offerings. For a cybersecurity firm, this may include assembling a team of experienced security analysts, penetration testers, incident responders, and technical support personnel.
According to a recent industry report, the global cybersecurity workforce shortage is estimated at 3.4 million positions, highlighting the importance of strategic talent acquisition and retention for cybersecurity startups. ShieldSecure Consulting must carefully assess its staffing needs, offering competitive compensation and benefits, and investing in continuous training and professional development to build a skilled and engaged cybersecurity team.
In addition to human resources, ShieldSecure Consulting will need to allocate resources for acquiring and maintaining the necessary technology infrastructure , such as secure data centers, cloud-based security platforms, and specialized cybersecurity tools and software. Careful budgeting and forecasting will be essential to ensure the business has the financial resources to fund these operational requirements.
- Explore opportunities for strategic partnerships and outsourcing to leverage specialized expertise and technologies without the need for significant capital investment.
- Implement robust business continuity and disaster recovery plans to ensure the seamless and uninterrupted delivery of cybersecurity services.
By meticulously outlining the operational processes and resource requirements, ShieldSecure Consulting can position itself to deliver consistent, high-quality cybersecurity services and build a sustainable, scalable business model. This level of operational planning and preparedness will be a key competitive advantage in the dynamic and rapidly evolving cybersecurity industry.
Assemble a Skilled and Experienced Cybersecurity Team
Building a strong, multifaceted cybersecurity team is a crucial step in developing a successful cybersecurity business plan. The team you assemble will be responsible for driving innovation, delivering high-quality services, and ensuring the long-term success of your venture. When constructing your cybersecurity team, it's essential to prioritize a balance of technical expertise, industry experience, and strategic thinking.
First and foremost, recruit talented and qualified cybersecurity professionals who possess the necessary skills and knowledge to protect your clients' digital assets. This may include roles such as information security analysts, penetration testers, incident response specialists, and cybersecurity architects. Seek individuals with a proven track record of implementing effective security measures, detecting and mitigating threats, and staying up-to-date with the latest cybersecurity trends and best practices.
- Offer competitive salaries and benefits to attract top-tier talent in the cybersecurity field.
- Prioritize candidates with industry certifications, such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH), to ensure a high level of expertise.
- Consider building a diverse team that combines technical skills with complementary expertise, such as risk management, compliance, and project management.
In addition to technical expertise, your cybersecurity team should also include individuals with strong business acumen and strategic thinking . These individuals will be responsible for aligning your cybersecurity services with the unique needs and pain points of your target market, as well as developing effective marketing and sales strategies. Look for team members with experience in areas such as business development, client relations, and project management to ensure a well-rounded approach to your cybersecurity venture.
Lastly, consider building strategic partnerships and alliances with other cybersecurity providers, industry experts, and complementary service providers. These partnerships can help you expand your service offerings, access a wider pool of talent, and stay ahead of the curve in an ever-evolving cybersecurity landscape. Collaborate with these partners to share knowledge, resources, and best practices, ultimately strengthening your team's capabilities and your business's overall competitiveness.
According to a 2022 report by MarketsandMarkets , the global cybersecurity market is expected to grow from $167.1 billion in 2020 to $281.7 billion by 2025 , at a CAGR of 11.0% during the forecast period . To capitalize on this rapidly expanding market, it's essential to assemble a skilled and experienced cybersecurity team that can deliver exceptional services, drive innovation, and ensure the long-term success of your business.
Related Blogs
- Cyber Security Business Idea Description in 5 W’s and 1 H Format
- Cyber Security Company Owner Earnings: A Breakdown
- How to Open a Cyber Security Career: Steps to Break In
- 7 Critical KPIs for a Cyber Security Business
- How to Optimize Cybersecurity Operating Costs
- How to Enhance Profitability in Cybersecurity Business
- How Much Does It Cost To Establish A Cybersecurity Firm?
Leave a comment
Your email address will not be published. Required fields are marked *
Please note, comments must be approved before they are published

IMAGES
VIDEO